Two-Factor Authentication
vs. Biometrics Authentication
More often than not, the
argument over the implementation of biometric authentication brings us to a
counter-solution: two-factor authentication (TFA, for short). Many argue that
TFA allows for greater security (than the typical single-password authentication),
without needing very much of a user’s personal information. However, others do
not find TFA’s “additional security” significant enough for TFA to constitute
as a valid security improvement, bringing us to the solution of biometric
authentication. In this article, we will examine and compare the two options:
two-factor authentication and biometrics authentication.
Let’s begin by pointing out
that TFA’s concept is not entirely new. We have all used it, for example, when
using a debit card: both the debit card and a PIN number are required to
retrieve one’s banking information. Simply put, TFA, also known as two-step
verification, is a means of
authentication that requires two of the following authentication factors: a knowledge
factor (something the user knows), a possession factor (something
the user has), and an inherence factor (something the user is).
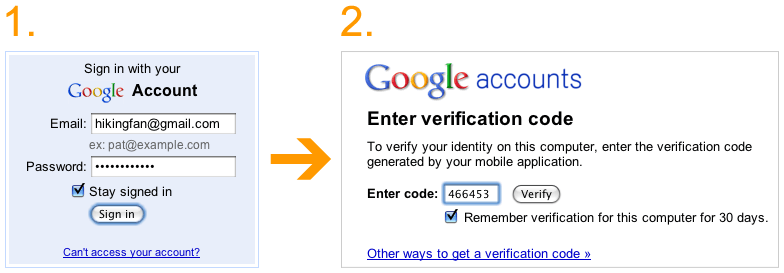
Google, PayPal and DropBox have recently implemented this system. Users can elect to have a two-step
verification system to protect their accounts; they first login with their
username + password, and then are sent a text message with a verification code
that is required as a “second password”.
Historically,
TFA has been viewed as overly complicated, requiring too many moving parts and
results in a less efficient, less expedient Internet experience. This also requires
users to have their possession factor (their cell phones) at all times. In
addition, System
Administrators hate the overhead on their systems and the extra points of
failure.
These factors (as well as others) have hindered the growth of
TFA, regardless of its additional security.
On
the other hand, Jeff Atwood, a software developer, author, and co-founder of
the programming question-and-answer site Stack Overflow explained:
“Yes,
it’s a bit cumbersome, but this process is inconvenient in the same way that
bank vaults and door locks are. The upside is that once you enable this, your
e-mail becomes extremely secure.”
Now
we can compare TFA to at a different solution: biometric authentication.
Relative to TFA, biometric authentication is more efficient and expedient. In
theory, the system is great being that you can’t “lose” your fingerprint or
retina, you can’t forget it, and it is unique to you. Its uniqueness, however,
can be seen as both a pro and a con.
While it does allow for great security in
that each user has a distinct “password”, it also allows for not-so-great
security in that once that fingerprint or retina scan is lost…you’re screwed.
Furthermore, current scanners cannot distinguish whether fingerprints are from
a real finger or an artificial one. In which case, if a hacker really wants to
find another person’s personal data, he can most likely artificially recreate
his/her fingerprint. (We have to also realize that this sort of hacking is significantly more difficult than
finding one’s password).
Simple
question: what do you think? Is the additional security of biometric
authentication worth the risk of possibly losing data as crucial as your
fingerprint? Should we avoid such a possible dilemma and stick with two-factor
authentication, regardless of its inefficiency/inexpedience?

I think its an interesting point considering whether biometric authentication is useful as a standalone or whether it better augments existing two-factor authentication. Arguments can certainly be made that biometric authentication is more effective as a secure password than nearly anything else. Yet, these are obvious risks as you mentioned above with losing the retina scan or fingerprint in a data file, not to mention security risks that can be posed with taking an individual biological identity. So, first do you believe that biometric authentication can function as a standalone authentication service?
ReplyDeleteI personally believe that that biometric authentication is risky to use by itself especially for items or information of a high importance/value.
However, considering two-factor authentication - the traditional two-factor authentication may, as you mentioned, rely on something that you 'know' and something that you 'have.' This might include a password paired with a credit card. It is definitely harder to steal an identity if these two authentication methods are needed. However, taking into account the 'modern' definition two-factor authentication: the use of two out of three authentication techniques (something that you 'know,' 'have,' and 'are'). It appears that biometric authentication can, in fact, be part of this TFA ideology. So, in some sense the question is invalid, since biometric authentication can be a part of two-factor authentication.
Another interesting scenario to note is the situation in which a particular authentication is needed. For example - logging into your laptop. If you argue that a simple password is not sufficient authentication, then the user can opt to include fingerprint recognition as a password setting. However, it seems unreasonable to use TFA as you posed it in the article above - since most people do not carry around a physical 'key' to their laptop. Additionally, in this scenario strides have been taken to make passwords more secure by including a graphical password. Microsoft recently made a graphical password authentication service that is more secure than traditional text-based passwords. (see: http://blogs.msdn.com/b/b8/archive/2011/12/16/signing-in-with-a-picture-password.aspx) However, this still fits under one-factor of authentication types. I believe that the two factors used depends on the situation itself, and as such not all devices/information requires more than 1-factor authentication, while diametrically opposite items might require all three-factors of authentication.
Biometric authentication likely will not replace password authentication until the technology becomes ubiquitous. However, I can see strides being made in that direction, which is promising since biometric authentication certainly proves to be more convenient than any other methods.
Regarding an initial question though, I do not believe that biometric authentication by itself is more secure than any two-factor authentication. I believe that two-factors no matter what the factor is, is automatically more secure by virtue of needing two different bits of information for authentication to be processed.
Interesting analysis. The three-factor analysis (possession, inherent, and remembered) seems like a very useful way to think about the alternatives here. As Tara points out, it may always be that 2 of 3 is needed. Of course this doesn't cover all of the risk cases. One is that a malicious system (e.g., loggin in on a public machine) might capture both biometric and password-like information and then reuse them. Another is cases like hostile interrogation, where the user is forced to hand over physical objects, reveal passords, and provide physical authentication. But it isn't clear that anything can solve this kind of threat.
ReplyDeleteDebit cards are often not an example of two factor authentication. If you give me your debit card number (knowledge), I can use it to buy stuff online.
ReplyDeleteHow are biometrics different from two factor authentication? They involve something you know and something you have (your fingerprints, your retinas, etc). The only difference seems to be that it's a little harder for someone to steal a fingerprint than a cell phone (and that it's harder to get a new set of fingerprints if your set is compromised).
The security checkpoints
ReplyDeletethat focus on detecting weapons and other prohibited items (like the one at your airport) only do half the job. This means airport environments are not safe. The security procedures work mainly on detecting items, because security screening transient passengers is a complicated task. But by not focusing on people, they miss the point entirely: a weapon may be a threat in the wrong hands, but the wrong hands in a sensitive area are ALWAYS a threat! This is how the professionals focus their security efforts on people and not just items they carry to ensure proper security is maintained.